Law enforcement this week turned the tables on LockBit, one of the most notorious ransomware gangs, locking the hackers out of their own servers and locking up at least two of their members. Operation Cronos, the coordinated international effort to bring down the gang, is already reaping benefits for some of the victims locked out of their own IT systems.
The UK’s National Crime Agency, FBI and Europol have obtained over 1,000 decryption keys and are in the process of contacting companies to help them recover encrypted data.
Since January 2020, the LockBit ransomware gang has executed over 2,000 attacks against targets such as the UK’s Royal Mail, hospitals, schools and businesses across a range of industries, issuing hundreds of millions of U.S. dollars in ransom demands and causing billions in damage due to disruptions to operations and loss of critical information and data.
When a victim’s network was infected by LockBit’s malicious software, their data was stolen and their systems encrypted. A ransom would be demanded in cryptocurrency for the victim to decrypt their files and prevent their data from being published.
Crippling LockBit required a coordinated effort between Britain’s National Crime Agency (NCA), the U.S. Federal Bureau of Investigation, Europol, and a coalition of international police agencies,
Ransomware-As-A-Service
LockBit first emerged at the end of 2019, since then it has grown rapidly and in 2022 it became the most deployed ransomware variant across the world, according to Europol.
The group is a ‘ransomware-as-a-service’ operation, meaning that a core team creates its malware and runs its website, while licensing out its code to affiliates who launch attacks.
LockBit’s established a global presence, with hundreds of affiliates recruited to conduct ransomware operations using LockBit tools and infrastructure, according to Europol. Ransom payments were divided between the LockBit core team and the affiliates, who received on average three-quarters of the ransom payments collected.
The ransomware group is also infamous for experimenting with new methods for pressuring their victims into paying ransoms. Triple extortion is one such method which includes the traditional methods of encrypting the victim’s data and threatening to leak it, but also incorporates Distributed Denial-of-Service (DDoS) attacks as an additional layer of pressure.
The gang’s move to triple extortion was partly influenced by a DDoS attack they themselves experienced, which impeded their ability to publish stolen data. In response, LockBit enhanced their infrastructure to resist such attacks.This infrastructure is now under law enforcement control.
The Chronos operation included the take down of 34 servers in the Netherlands, Germany, Finland, France, Switzerland, Australia, the United States and the United Kingdom, according to Europol.
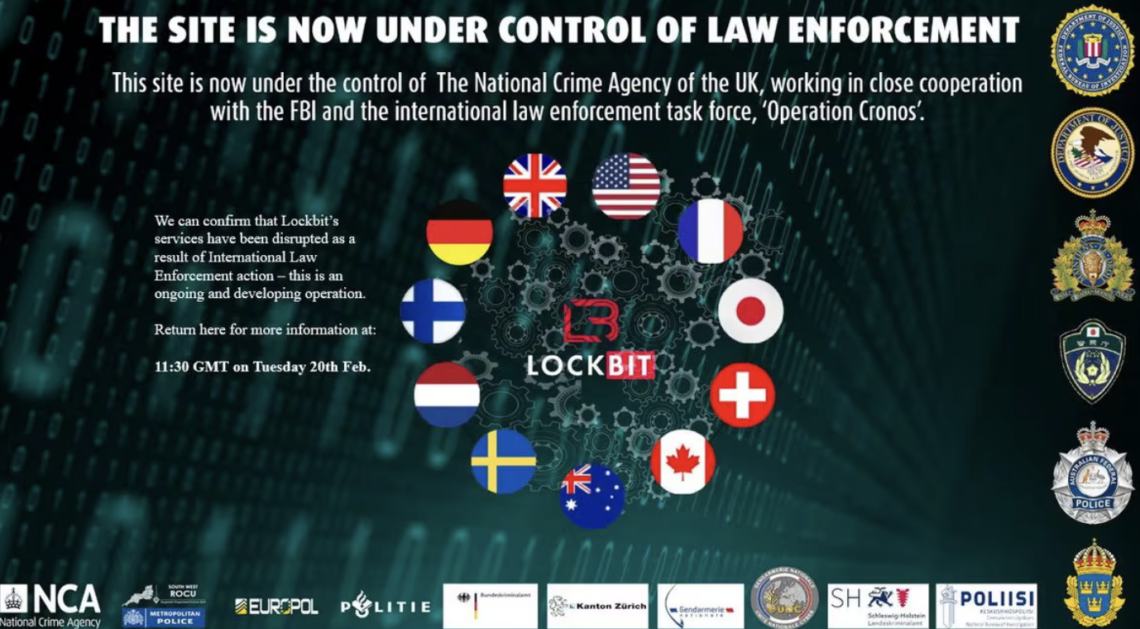
LockBit’s website on the Dark Web has also been taken down and replaced by a message stating that the site is “now under control of law enforcement”. (see the screenshot from the UK’s NCA site). Officials have used the seized web page to taunt the hackers with forthcoming releases exposing LockBit’s private information about its capabilities and operations. The site now also advertises access to tools for victims of the ransom-seeking gang to decrypt their data. These solutions have been made available for free on the ‘No More Ransom’ portal, available in 37 languages.
Law enforcement agencies involved in Operation Cronos also said they froze about 200 cryptocurrency accounts and seized a “wealth of data” to fuel the investigation. “
The UK’s National Crime Agency (NCA) has obtained LockBit platform’s source code and a vast amount of intelligence from their systems about their activities and those who have worked with them .
Some of the data on LockBit’s systems belonged to victims who had paid a ransom to the threat actors, evidence that “even when a ransom is paid, it does not guarantee that data will be deleted, despite what the criminals have promised,” the NCA said in a press release.
More Arrests Are Likely
Law enforcement officials said the technical infiltration and disruption is only the beginning of a series of actions against LockBit and its affiliates. In wider action coordinated by Europol, two LockBit actors were arrested on February 20 in Poland and Ukraine.
The U.S. Department of Justice has announced that two defendants responsible for using LockBit to carry out ransomware attacks have been criminally charged, are in custody, and will face trial in the U.S. The US has also unsealed indictments against two further individuals, who are Russian nationals, for conspiring to commit LockBit attacks.
.More arrests are likely. The U.S. State Department is offering a $10 million reward for information leading to the identification or location of any individual(s) who hold a key leadership position in the crime group and $5 million for information leading to the arrest of anyone who has participated in LockBit ransomware activities.
“The impact of the LockBit take down “will be significant and will likely affect other threat actors, the Chief Intelligence Officer at cyber threat intelligence company Prodaft said in an email interview with The Innovator. While there is the possibility that some members will regroup and establish new ransomware groups “law enforcement has already amassed a substantial amount of intelligence and will be able to track them easily whenever they join a new team or engage in malicious activities,” he says.
Prodaft said it has been actively assisting law enforcement to identify distinctive tactics, techniques and procedures employed by Lockbit affiliates; gain insight into affiliate infrastructures and ties to other criminal gangs such as EvilCorp, Fin7 or Wizard Spider; acquire crucial source code and related access keys; and vigilantly monitor so-called initial access brokers since the inception of Lockbit’s involvement in the cybercrime landscape.
“Law enforcement has aided numerous victims in decrypting files,” says Prodaft’s Chief Intelligence Officer, who declined to have his name released publicly. “The precise number of victims remains unknown. We can only confirm that our assistance facilitated the decryption software for over 50 companies.”
While law enforcement’s seizure this week of a 1000 decryption tools is likely to help a larger number of victims, corporate chief information security officers (CISOs) should not let their guard down, says Prodaft’s Chief Intelligence Officer. “LockBit may be down but there is always some new ambitious threat actor out there and they are getting increasingly sophisticated and ruthless.”
IN OTHER NEWS THIS WEEK
ARTIFICIAL INTELLIGENCE
U.S. Justice Department Names First AI Officer
The U.S. Justice Department on February 22 named Jonathan Mayer, a professor at Princeton University who researches technology and law, as its first official focused on artificial intelligence as the department grapples with the potentially transformative affects of AI on federal law enforcement and the criminal justice system.
Adobe Brings Conversational AI to Trillions of PDFs
Adobe introduced AI Assistant in beta, a new generative AI-powered conversational engine in Reader and Acrobat, which aims to unlock new value from the information inside the approximately 3 trillion PDFs in the world. AI Assistant, which will be integrated into Reader and Acrobat workflows, will generate summaries and insights from long documents, answers questions and formats information for sharing in emails, reports and presentations, the company said.
Tech Giants Sign Pledge To Fight AI Election Interference
A group of 20 tech companies have agreed to work together to prevent deceptive artificial-intelligence content from interfering with elections across the globe this year. The rapid growth of generative AI which can create text, images and video in seconds in response to prompts, has heightened fears that the new technology could be used to sway major elections this year, as more than half of the world’s population is set to head to the polls.
ENERGY
Scientists Say AI Removes One Of The Big Roadblock To Fusion Energy
Researchers from Princeton University and the Princeton Plasma Physics Laboratory reported in the journal Nature they found a way to use AI to forecast potential instabilities that have long hindered fusion energy and prevent them from happening in real time. The team carried out their experiments at the DIII-D National Fusion Facility in San Diego, and found that their AI controller could forecast potential plasma tearing up to 300 milliseconds in advance. Without that intervention, the fusion reaction would have ended suddenly. The findings are “definitely” a step forward for nuclear fusion, Egemen Kolemen, a professor of mechanical and aerospace engineering at Princeton University and an author on the study, told CNN.
HEALTH
Neurolink Says First Human Patient Able To Control Computer Mouse Using Their Thoughts
The first human patient implanted with a brain-chip from Neuralink appears to have fully recovered and is able to control a computer mouse using their thoughts, the startup’s founder Elon Musk said February 19. The devices could be used to treat conditions like obesity, autism, depression, and schizophrenia.
SUSTAINABILITY
Saudi Firm Alat Announces Sustainable Manufacturing Partnerships
Saudi Arabian tech company Alat, owned by the country’s Public Investment Fund, this week announced partnerships with four companies including Softbank Group and Carrier Corp as it seeks to create a sustainable manufacturing hub in the kingdom. Alat is also partnering with China’s Dahua Technology and The Saudi Technology and Security Comprehensive Control Company (Tahakom), it said, and will support them in reducing their emissions and moving towards carbon zero manufacturing.
To access more of The Innovator’s News In Context articles click here.